sudo ansible-galaxy install rhtps.800-53 -p /etc/ansible/rolesIn this exercise, we are going to use Ansible Tower to run DISA STIG and NIST 800-53 evaluations of our environment. Note that the NIST 800-53 role also includes the execution of DISA STIG evaluation against targeted hosts.
-
DISA STIG controls https://galaxy.ansible.com/MindPointGroup/RHEL7-STIG/
-
NIST 800-53 controls https://galaxy.ansible.com/rhtps/800-53/
Adding the DISA STIG and NIST 800-53 role to your Tower node
Step 1: Download role to Ansible roles directory
In your wetty window (if you closed it, see the SETUP step, in your workbook), type the following:
You will then see the following, showing that the role has been downloaded to your system-wide Ansible roles directory, /etc/ansible/roles:
- downloading role '800-53', owned by rhtps
- downloading role from https://github.com/rhtps/ansible-role-800-53/archive/v1.1.1.tar.gz
- extracting rhtps.800-53 to /etc/ansible/roles/rhtps.800-53
- rhtps.800-53 (v1.1.1) was installed successfullyStep 2: Select Projects
First, in Ansible Tower, click on ![]()
Step 3: Click uploaded
Next, Select ADD ![]()
Step 4: Complete the Project form
Complete the form using the following entries
NAME |
Ansible 800-53 Project |
DESCRIPTION |
800-53 Role Playbook |
ORGANIZATION |
Default |
SCM TYPE |
Git |
SCM URL |
|
SCM BRANCH |
|
SCM UPDATE OPTIONS |
|
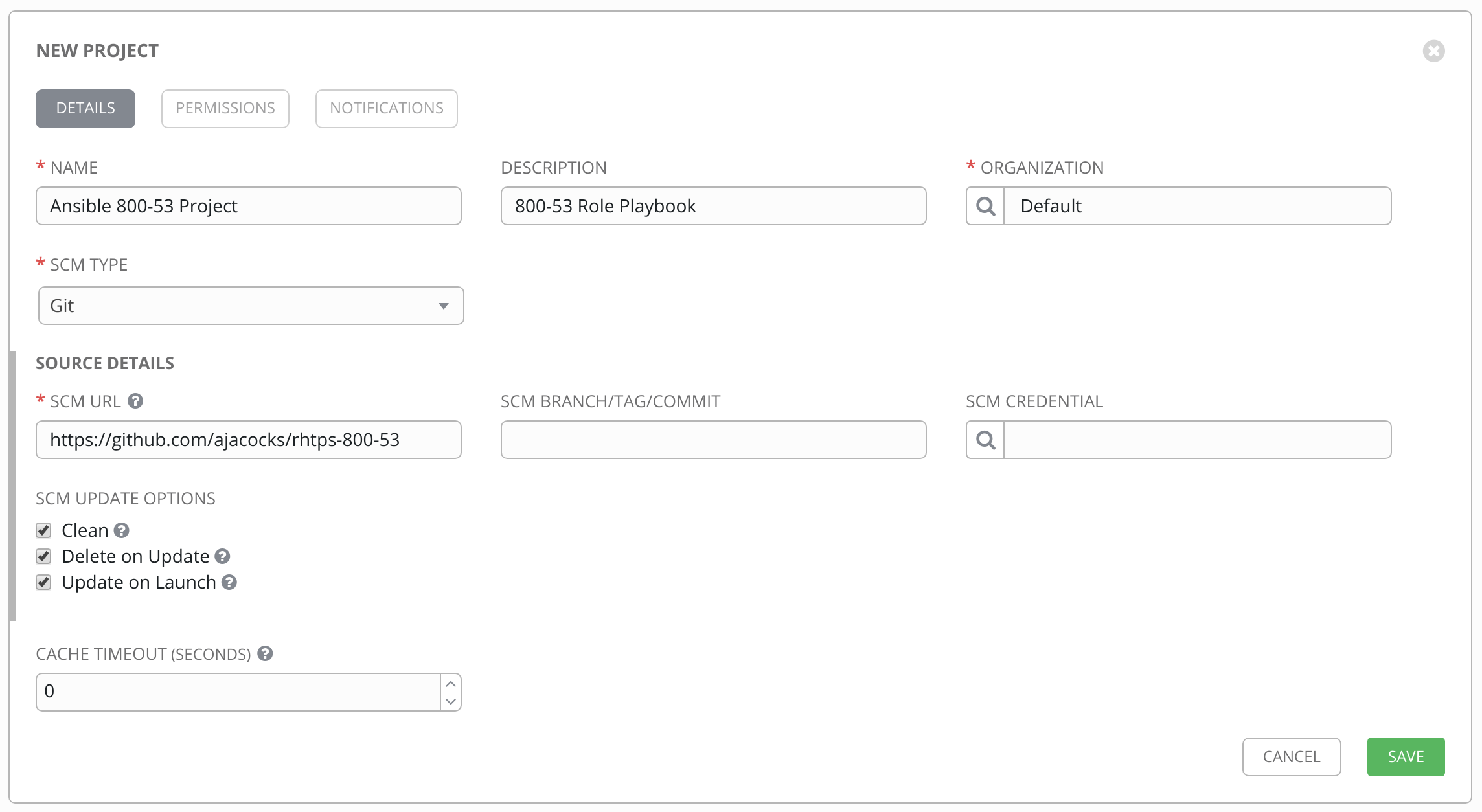
Step 5: Save
Select SAVE ![]()
Step 6: Select Template tab
In your Tower window, click TEMPLATES TEMPLATES
Step 7: Add the job template
Click ADD ![]() , and select
, and select JOB TEMPLATE
Step 8: Complete the job Template form
Complete the form using the following values. Note that the PLAYBOOK field should offer 800-53.yml as an option, when clicked.
NAME |
NIST 800-53 and DISA STIG Job Template |
DESCRIPTION |
Template for security playbooks |
JOB TYPE |
Run |
INVENTORY |
Ansible Workshop Inventory |
PROJECT |
Ansible 800-53 Project |
PLAYBOOK |
main.yml |
MACHINE CREDENTIAL |
Ansible Workshop Credential |
LIMIT |
web |
OPTIONS |
|
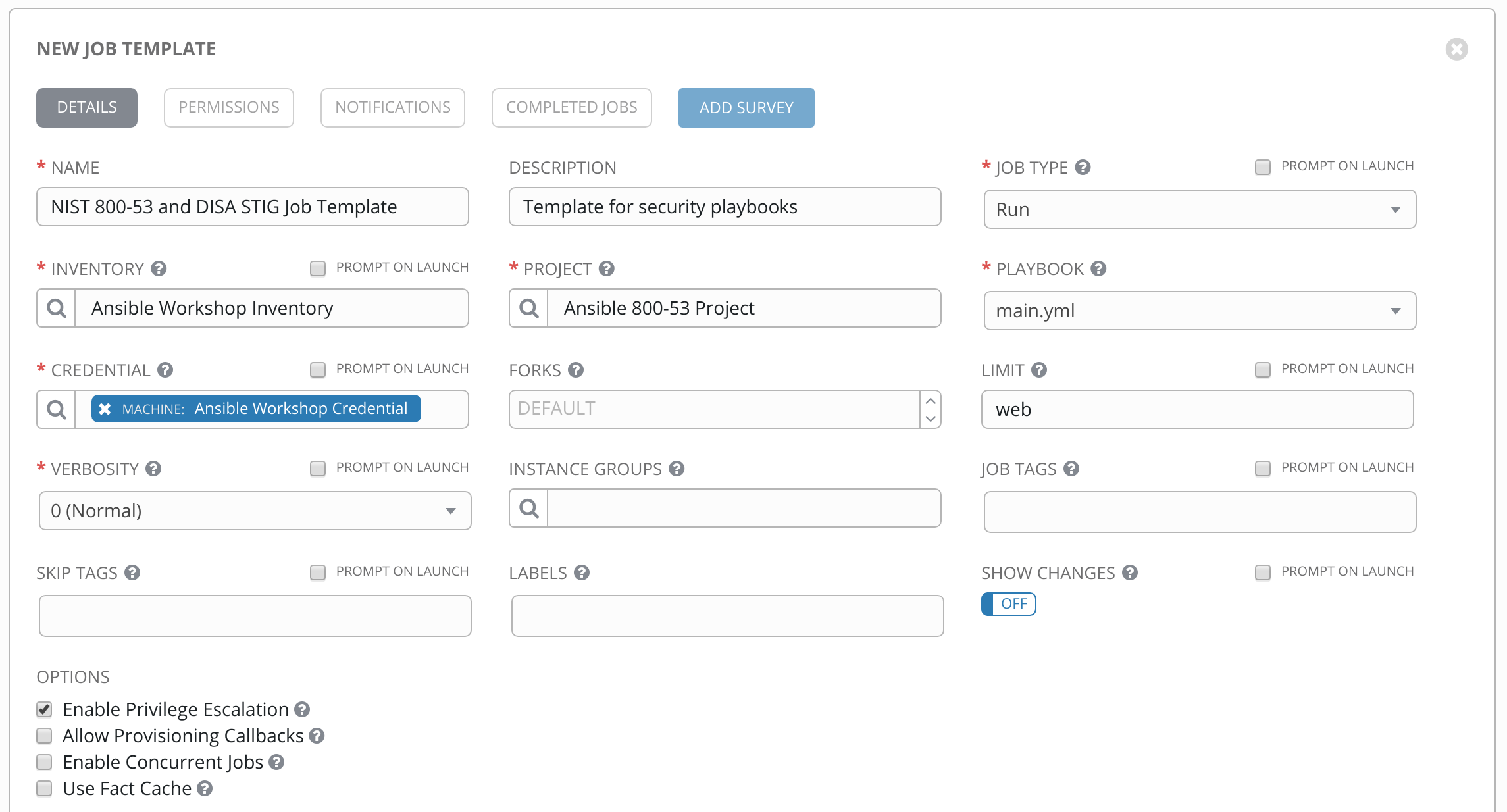
Step 9: Save the template and run it
Click SAVE  , to store your new template, and we are ready to run it.
, to store your new template, and we are ready to run it.
Click on the rocket ship icon ![]() next to the
next to the NIST 800-53 and DISA STIG Job Template entry, to launch the job.
You can see what the job looks like, as it is executing, and what the SCAP results look like, when uploaded to your second node, in the panel, below.
Step 10: Observe the scanning process and view reports
You can watch the scan run against your managed node. Note that each compliance check is named and detailed.
Once the check is complete, you can open a new tab in your web browser, and navigate to the following URL, where workshopname is the workshop prefix, and # is the number that your instructor gave you:
http://example-node0.example.redhatgov.io/scapClick on the link called scan-xccdf-report-… to refiew the SCAP report that was generated. Note the failures in the report; look at the machines, if you want, via your Wetty ssh session, to see what the problems might be.
Workshop Details
|
|
|
|
| Domain: |

|
|
| Workshop Name: | ||
| Region: | ||
| User ID: |

